Three Traps of WPA Transition Modes
By Eva Santos On 02/06/2025
Transition Modes have existed as a means to bridge the gap between new technology requirements and client incapabilities in the Wi-Fi space. However, understanding what these modes mean for the client devices is key to picking the appropriate settings for a network. It turns out, these transition modes don't do as much as we may assume and consequently have security and client compatibility implications. Here are three traps of transition modes to watch out for and alternatives for each situation.
Trap 1: Using WPA3-Personal Transition mode isn't necessarily better than WPA2-Personal
WPA3-Personal Transition mode allows clients that only support WPA2-PSK to use the same SSID as those that support WPA3-SAE. Despite its ease of deployment and solution for enterprises with complex roaming requirements, it doesn't make a migrated SSID as secure as one may think.
This example WPA3-Personal Transition mode SSID allows for Management Frame Protection to be enabled, but not required. It offers two Auth Key Management (AKM) suites: AKM 2 for PSK and AKM 8 for SAE.
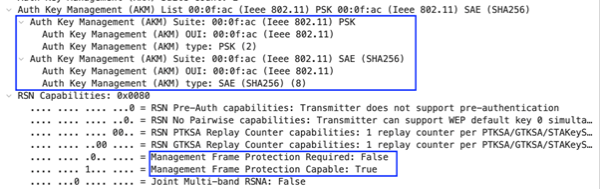
As a result, the SSID will still permit WPA2-PSK only clients that do not have MFP/802.11w support to connect. Using MFP to obscure management frames would make hacking through the passphrase more difficult. WPA2-PSK has vulnerabilities stemming from the ability to break the preshared key derivation and discover the SSID's password. By allowing devices with this vulnerability onto the same SSID, any security merit is lost from WPA3; Hackers can gain access to the whole Basic Service Set (BSS) and proceed with other attacks on the network.
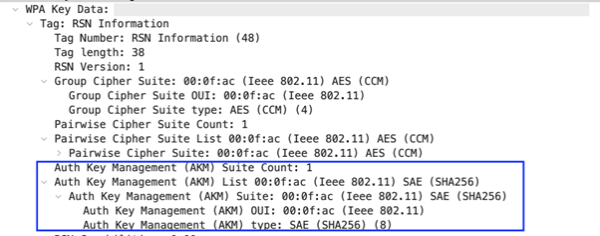
In situations where the client can use both WPA2-PSK and WPA3-SAE, EAPoL frame message 2 will confirm which AKM the client used. In the same WPA3-Personal Transition mode SSID shown in the previous picture, the client sends this EAPoL frame message 2. In the RSN Information tag within the WPA Key Data attribute, only AKM 8 for SAE is listed for the AKM Suite that the client used in the four-way handshake.
Administrators are better off separating WPA2-PSK and WPA3-SAE clients onto separate SSIDs; this way, administrators can reduce the potential attack surface to only WPA2-PSK clients. If the WLAN must support WPA2 for internal purposes, use a passphrase with sufficient complexity. A long passphrase is the easiest way to accomplish this.
Trap 2: Using WPA3-Enterprise Transition Mode doesn't introduce any new encryption ciphers or significant differences from WPA2-Enterpise
From a protocol standpoint, WPA3-Enterprise Transition Mode is almost the same as WPA2-Enterprise with MFP/802.11w set as enabled. Unlike WPA3-Enterprise which requires MFP, WPA3-Enterprise Transition Mode allows for MFP to be enabled or required, but not completely disabled. Per the WPA3 Specification:
"When an AP's BSS is operating in WPA3-Enterprise Transition Mode:
1. The AP's BSS Configuration shall enable at least AKM suite selectors 00-0F-AC:1 (IEEE 802.1X with SHA-1) and 00-0F-AC:5 (IEEE 802.1X with SHA-256) in the BSS.*
2. The AP's BSS configuration shall be PMF Capable, i.e., AP sets MFPC to 1 and MFPR to 0".(1)
*AKM suite 00-0F-AC:1 is disallowed for EHT (Wi-Fi 7) STAs.
Here is an example of a WPA3-Enterprise Transition SSID with MFP as enabled. Fast Transition(FT)/802.11r is set to disabled. The image below shows the RSN Information tag within a Beacon frame.
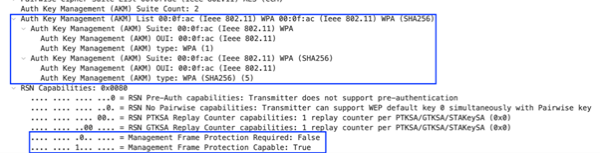
As the specification states, Management Frame Protection Required is set to 0 (False) and Management Frame Protection Capable (MFPC) is set to 1 (True). Additionally, the Auth Key Management (AKM) attribute shows two suites allowed: AKM 1 for "IEEE 802.1X with SHA-1" and AKM 5 for "IEEE 802.1X with SHA-256".
Enabling WPA3-Enterprise Transition Mode while requiring MFP brings it closer to WPA3-Enterprise requirements. AKM 1 will not show anymore. This second example is also of a WPA3-Enterprise Transition SSID with FT/802.11r is set to disabled, but this time MFP is set to required. This beacon only advertises AKM 5.
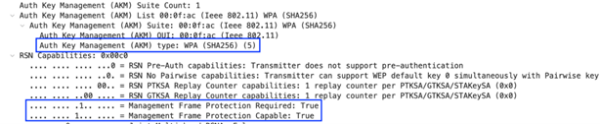
Even so, SSIDs cannot use WPA3-Enterprise Transition mode on 6 GHz band due to 6 GHz requiring MFP so it will not aid in transitioning a network into fresh 6 GHz spectrum.
When using FT/802.11r with MFP as enabled, AKM 3 for "FT Authentication over IEEE 802.1X using SHA-256" will also show in WPA3-Enterprise Transition mode.
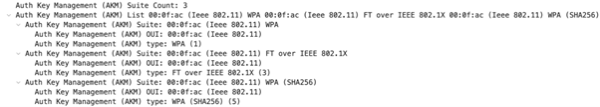
Likewise when performing the same with MFP as required, AKM 3 and 5 are advertised.
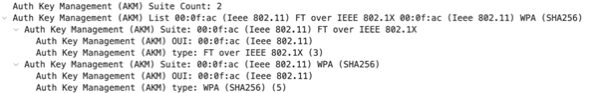
Now when comparing all this to a WPA2-Enterprise SSID with FT/802.11x and MFP set to enabled, it does not look much different. AKM 1 and 3 are advertised. We are only missing AKM 5 here.
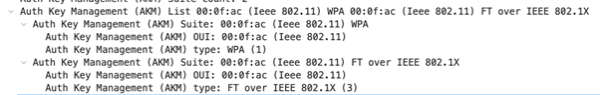
Unless the SSID requires MFP, a WPA3-Enterprise SSID will still advertise the older AKM 1 for devices not capable of AKM5 or AKM3 with FT enabled. Consequently, devices will remain vulnerable to downgrade attacks that force authentication at AKM1. For all scenarios shown, AES is used as the Pairwise/Group Cipher Suites. Therefore, WPA3-Enterprise Transition mode does not have much increased benefit compared to WPA2-Enterprise.
Trap 3: Transition Disable modes are complex and offer little value
The Wi-Fi Alliance introduced the "Transition Disable" feature to prevent downgrade attacks on clients that are both capable of WPA2 and WPA3 suites for Enterprise, Personal, and Open SSIDs. In Cisco's case, a 9800 Wireless Controller will "use the Transition Disable indication to disable transition modes for that network on a STA" (2) The practical result of this is often unintended behavior with clients that either support transition disable with flaws or do not support transition disable mode at all.
Even the Cisco Whitepaper states "This method is not generally recommended and should be enabled only when it is absolutely necessary." under this option. Having separated SSIDs per WPA mode is usually a better option to support most clients with the potential unintended behaviors of Transition Disable modes. An "absolutely necessary" use case for this would be having to support roaming under one SSID while supporting WPA3 whenever possible.
While the Wi-Fi Alliance has created these transition mode features to provide maximum flexibility for WLAN administrators, that doesn't mean administrators should use them. WLAN administrators should carefully weigh the network architecture and clients' capabilities against the security requirements for SSID before diving head first into these modes.
1. https://www.wi-fi.org/system/files/WPA3%20Specification%20v3.4.pdf
2.https://www.cisco.com/c/en/us/td/docs/wireless/controller/9800/technical-reference/wpa3-dg.html
Tagged with: cwnp, wireless networking, wpa, transition modes
Blog Disclaimer: The opinions expressed within these blog posts are solely the author’s and do not reflect the opinions and beliefs of the Certitrek, CWNP or its affiliates.